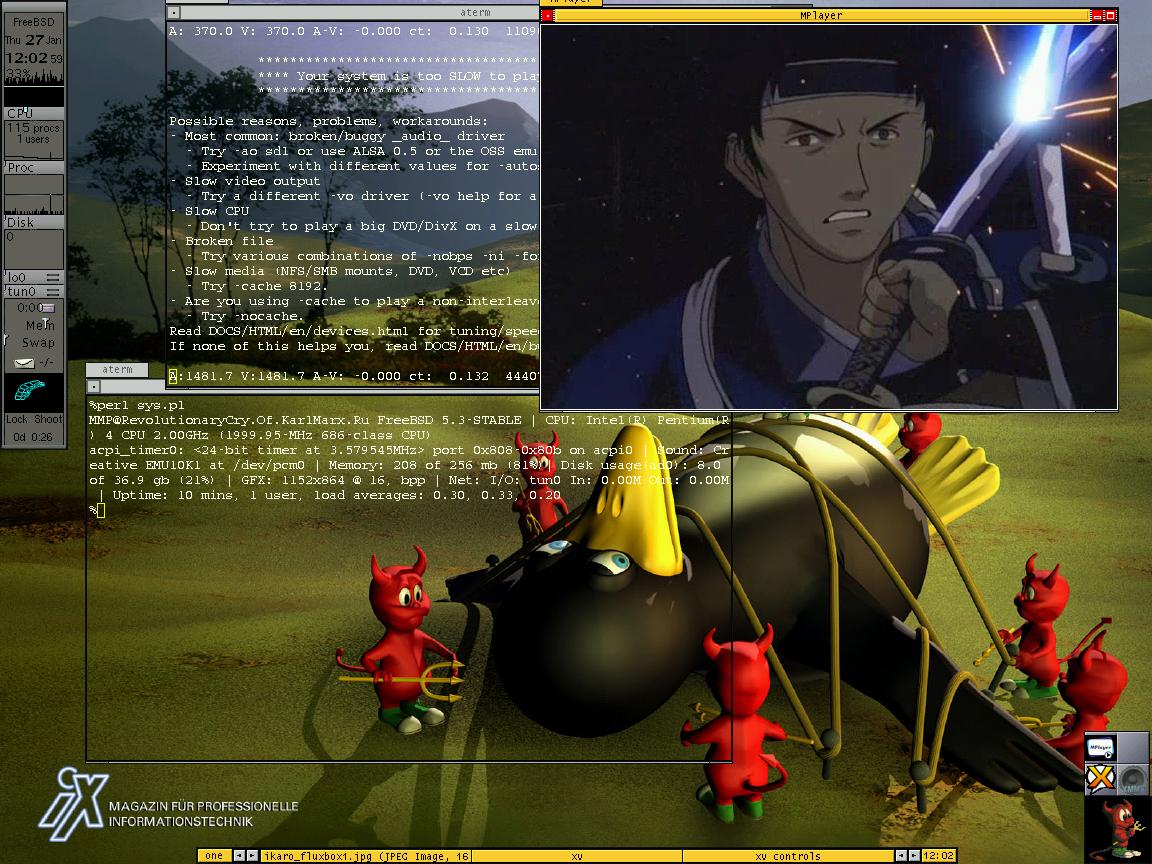
A hacker collective called “The Unknowns” has published Two Pastebin document that allegedly proves they managed to gain unauthorized access to a number of high profile websites.

The list of targets includes the Bahrain Ministry of Defense, Thai Royal Navy, a subdomain owned by car manufacturer Renault, Harvard University, French Ministry of Defense, Jordanian Yellow Pages, European Space Agency (ESA), US Military’s Joint Pathology Center, NASA’s Glenn Research Center and the US Air Force.
After hacking They Release Lots Of Screen Shots , Leaked Data , Admin Access In Pastebin In Two Docs.
1st Docs : Click here
2nd Docs : Click here
Message By The Attacker On Pastebin After The Attack :
A Message:
We are The Unknowns; Our Knowledge Talsk and Wisdom Listens...
Victims, we have released some of your documents and data, we probably harmed you a bit but that's not really our goal because if it was then all of your websites would be completely defaced but we know that within a week or two, the vulnerabilties we found will be patched and that's what we're actually looking for.
We're ready to give you full info on how we penetrated threw your databases and we're ready to do this any time so just contact us, we will be looking forward for this.
And for all the other websites out there: We're coming, please, get ready, protect your website and stop us from hacking it, whoever you are. Contact us before we take action and we will help you, and will not release anything... It's your choice now.
And for the Public: We're looking for your support... Support us to deliver our message to everyone out there...
We are The Unknowns; Our Knowledge Talsk and Wisdom Listens...

The list of targets includes the Bahrain Ministry of Defense, Thai Royal Navy, a subdomain owned by car manufacturer Renault, Harvard University, French Ministry of Defense, Jordanian Yellow Pages, European Space Agency (ESA), US Military’s Joint Pathology Center, NASA’s Glenn Research Center and the US Air Force.
After hacking They Release Lots Of Screen Shots , Leaked Data , Admin Access In Pastebin In Two Docs.
1st Docs : Click here
2nd Docs : Click here
Message By The Attacker On Pastebin After The Attack :
A Message:
We are The Unknowns; Our Knowledge Talsk and Wisdom Listens...
Victims, we have released some of your documents and data, we probably harmed you a bit but that's not really our goal because if it was then all of your websites would be completely defaced but we know that within a week or two, the vulnerabilties we found will be patched and that's what we're actually looking for.
We're ready to give you full info on how we penetrated threw your databases and we're ready to do this any time so just contact us, we will be looking forward for this.
And for all the other websites out there: We're coming, please, get ready, protect your website and stop us from hacking it, whoever you are. Contact us before we take action and we will help you, and will not release anything... It's your choice now.
And for the Public: We're looking for your support... Support us to deliver our message to everyone out there...
We are The Unknowns; Our Knowledge Talsk and Wisdom Listens...